October 2025 Quarterly Release
For help upgrading to the latest version, contact your Cloudhouse Representative. The following table describes each component available to upgrade within this release of Cloudhouse Guardian (Guardian). For more information on the known issues currently present within Guardian, see Known Issues.
Tip: To access a more simplified view of the changes included within this release, see October 2025 Changelog.pdf.
| Last Updated | Release Date | Guardian Platform | Guardian Web | Linux Agent |
|---|---|---|---|---|
| 3rd November 2025 | 29th October 2025 | V4 | V3.60.1 | V5.48.0 |
Guardian Web Application V3.60.1
Here's what's included in V3.60.1 of the Guardian web application as part of the October 2025 quarterly release.
New Features
The following new features are included within this release of the Guardian web application.
Improved Credentials Handling for Synchronize Nodes Scheduled Job
For Freshservice and ServiceNow integrations, when adding a Synchronize Nodes – Job Type, you can now use credentials stored in the Guardian vault or Secret Server to authenticate your access.
Note: For more information on each credential store, see Credentials and Secret Server Integration.
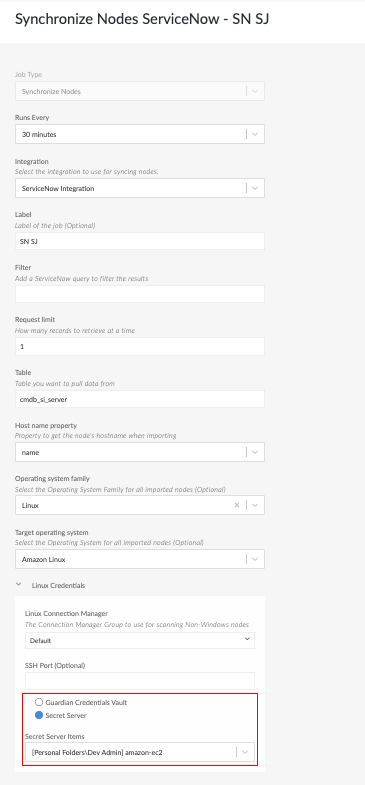
Instead of manually entering your Windows or Linux credentials each time, this enhancement allows you to securely authenticate using stored credentials, streamlining setup and improving security.
Search by External ID
The search bar on the Monitored tab (Inventory > Monitored) has been updated to enable you to search by external ID across each organizational unit (Node Groups, Environments, and Connection Manager Groups) in your Guardian instance. Previously, you could only search by external ID within the Node Groups drop-down menu. Now, this enhancement enables more robust search functionality across each of your assets.
Tip: An external ID is a unique identifier assigned to a node by an external provider, such as AWS or Azure, that can be used to identify a node outside of the more traditional node name or node type.
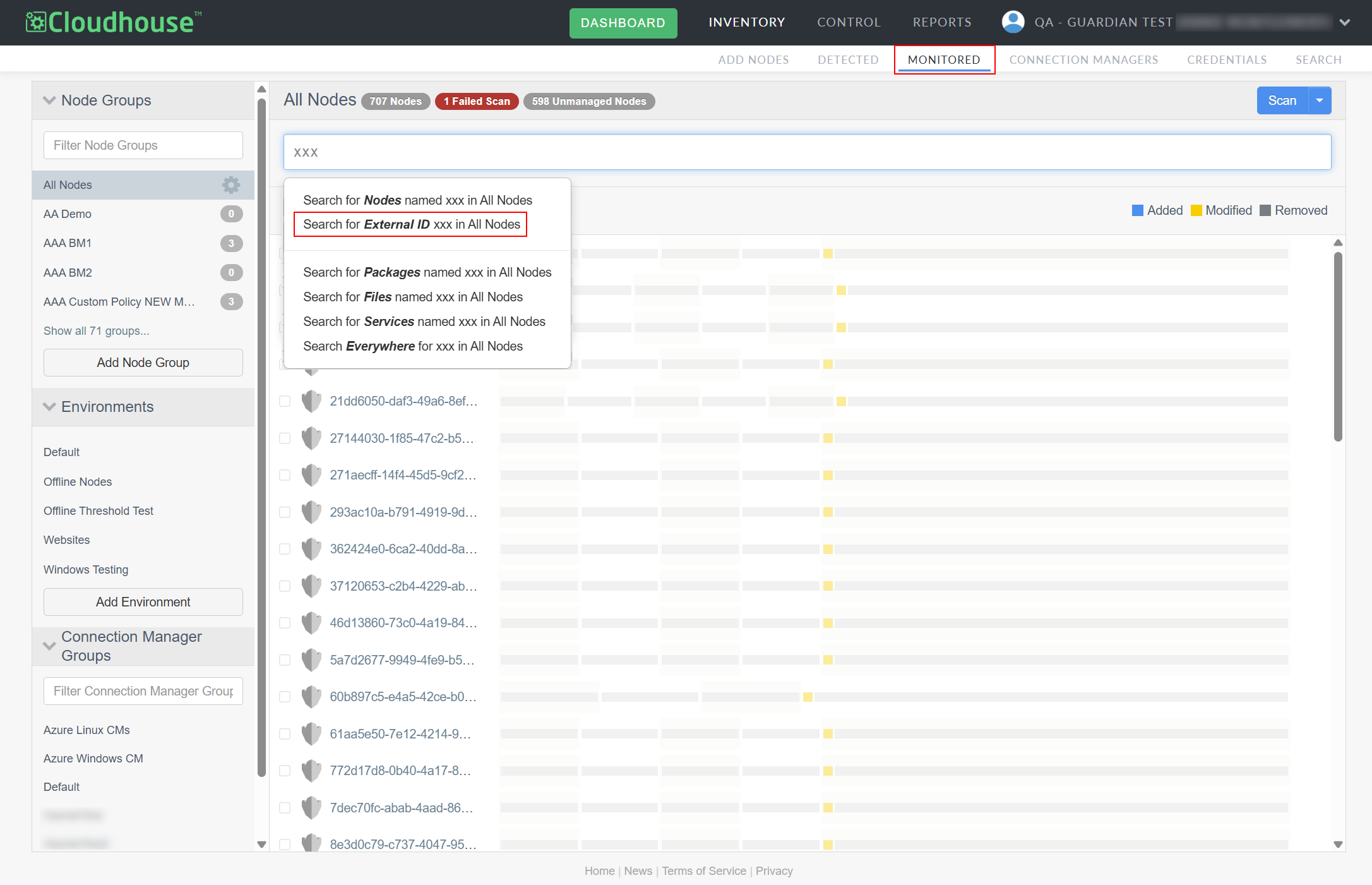
Note: For more information on using the search functionality in the Monitored tab, see Search Monitored Nodes.
New Event for Unsuccessful First Node Scan
We’ve updated the 'Node First Scanned' event to support better visibility and automation around unsuccessful first scans of newly added nodes. Previously, the 'Node First Scanned' event only triggered on successful first scans of a new node. This meant that if a node was added but failed to scan due to issues like misconfiguration, firewall blocks, or build errors – no event was generated, and the failure could go unnoticed in large-scale environments.
Tip: For more information on events, see Events.
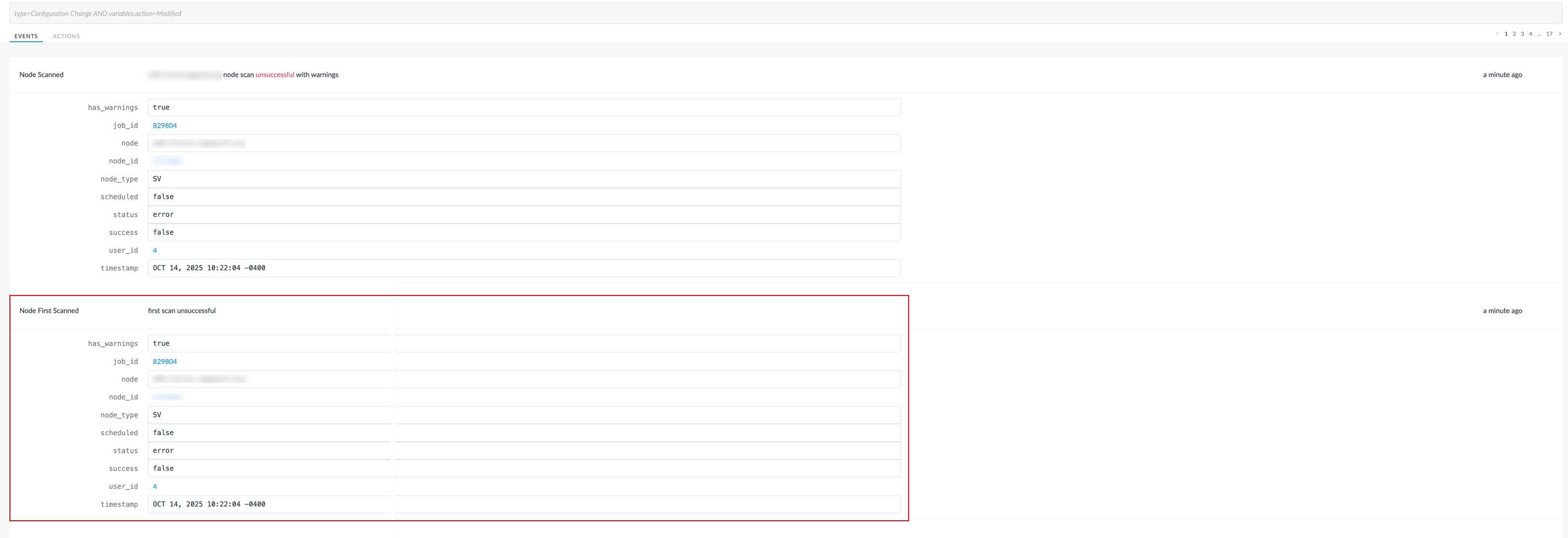
An event is now triggered when a first scan attempt fails for a newly added node. This enables automated incident reporting and remediation workflows for nodes that enter the system in a non-scanning state, ensuring visibility into failed first scans across thousands of nodes.
Other Enhancements
The following additional enhancements are included within this release of the Guardian web application.
Improved Banner Handling
We have decreased the display times for banners in Guardian to 1.5 seconds. Previously, banners (such as the following confirmation message, 'Policy successfully updated') were being displayed for up to 7 seconds, blocking the second top navigation menu during that time frame.
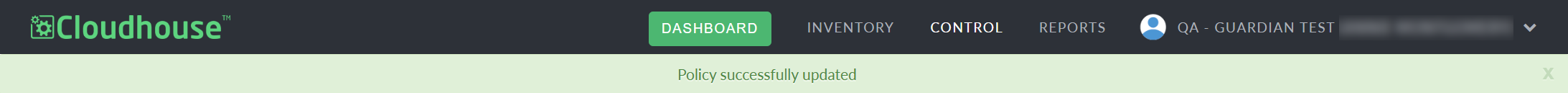
With the new, shortened display time, you can read the message displayed within the banner without any navigational abilities being impacted.
Change Reporting Improvements
As part of our continuous efforts to drive user experience and clarity, we have made the following improvements to the Change Report tab:
Tip: For more information on the Change Report tab, see Change Report.
-
Maximum Records Included in PDF Export – When exporting a change report as a PDF, all available records are now displayed within the report. Previously, the results were defined by the record Limit field in the Options drop-down menu.
Note: For more information on how to export a change report as a PDF, see Export a Report.
-
Improved Report Loading and Filter Response – We have significantly reduced the report loading time and removed distracting visual elements, such as the loading icon, making filter adjustments nearly instantaneous.
-
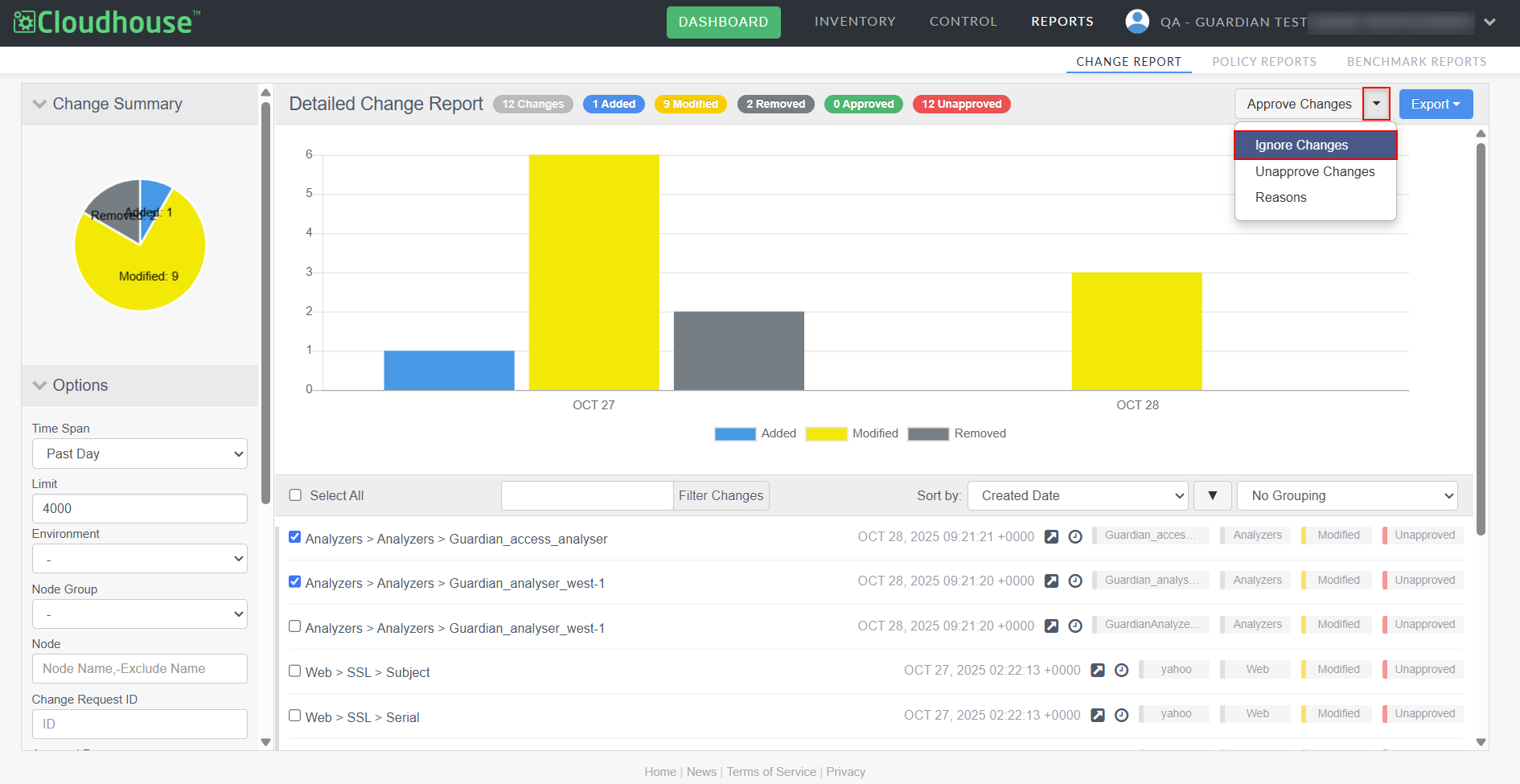
New Option to Ignore Changes – It is now possible to ignore one or more changes within the Change Report tab. Select the checkbox(es) of the change(s) you want to ignore, click the Approve Changes drop-down, and select Ignore Changes. Once a change is ignored, it is no longer visible on the node scan results page or within the Change Report tab.
Note: For more information, see Ignore Change.
-
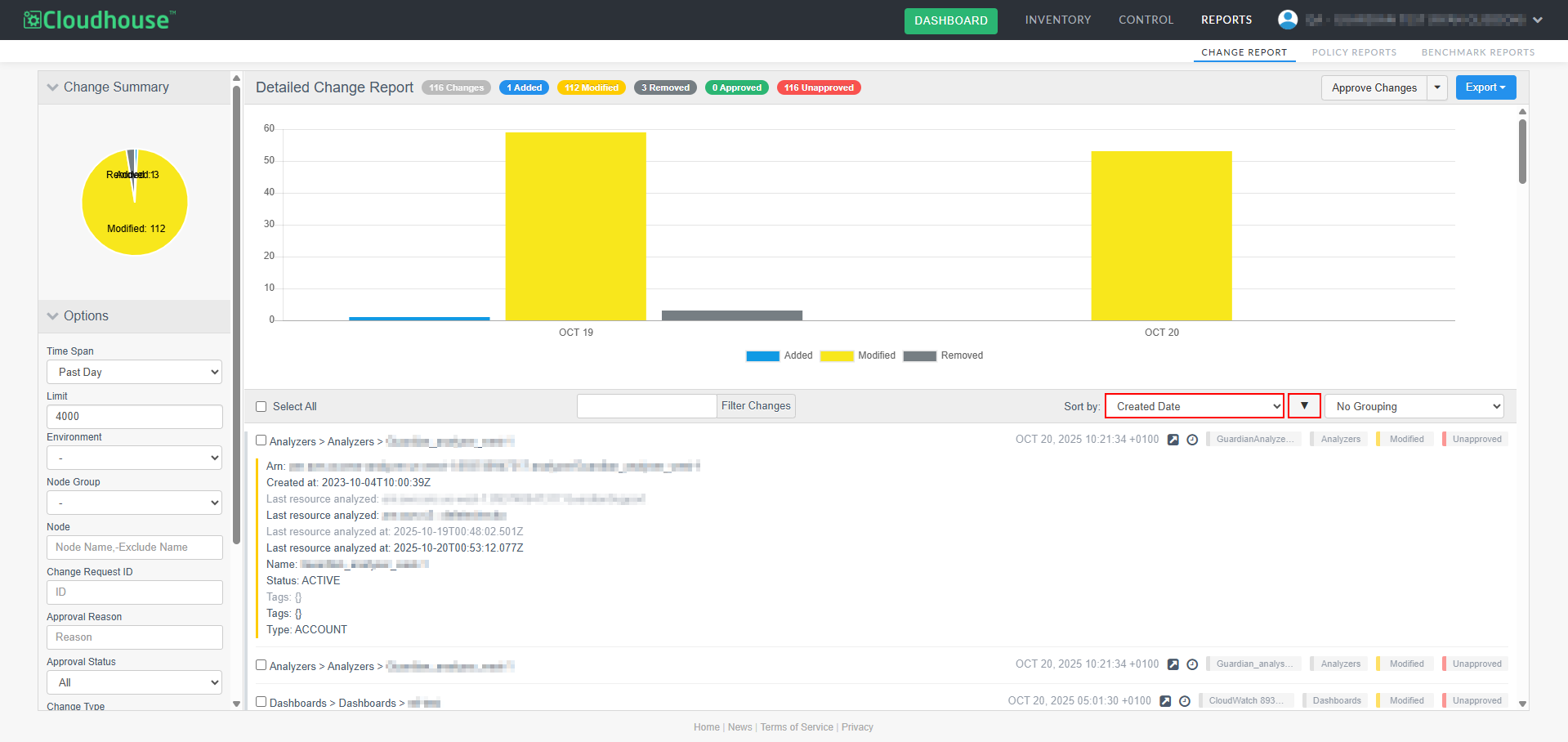
Sort Change Report by Key Fields – We have added the ability to sort by key fields in either ascending or descending order, making it easier to classify, review and prioritize changes, improving overall usability and efficiency. You can sort the change report using the following fields:
-
Path – The full path for the configuration item (CI), such as a file or folder.
-
Created Date – The time and date the change was made. The report is sorted by this field in descending order by default.
-
Node Name – Name of the node.
-
Change Type – The type of change (Added, Modified, Removed).
-
View All Elements for Modified Nodes
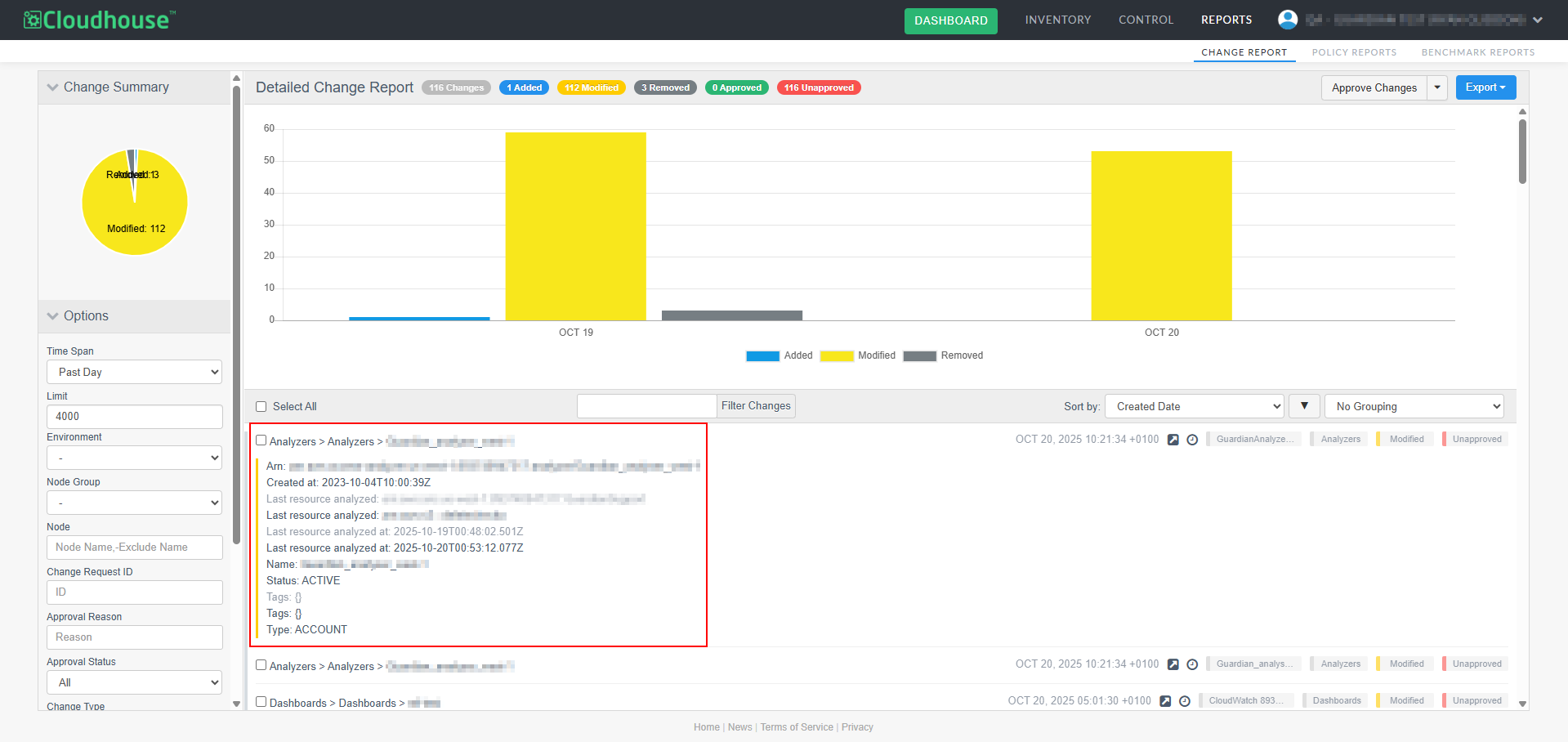
We’ve enhanced the Change Report tab to support a more comprehensive view of configuration changes. Previously, only the elements that had changed were displayed for modified nodes. Now, you can view all elements related to a changed node, including those that remained unchanged. This improvement provides greater context by allowing you to see the full state of a node at the time of change, useful for complex configurations.
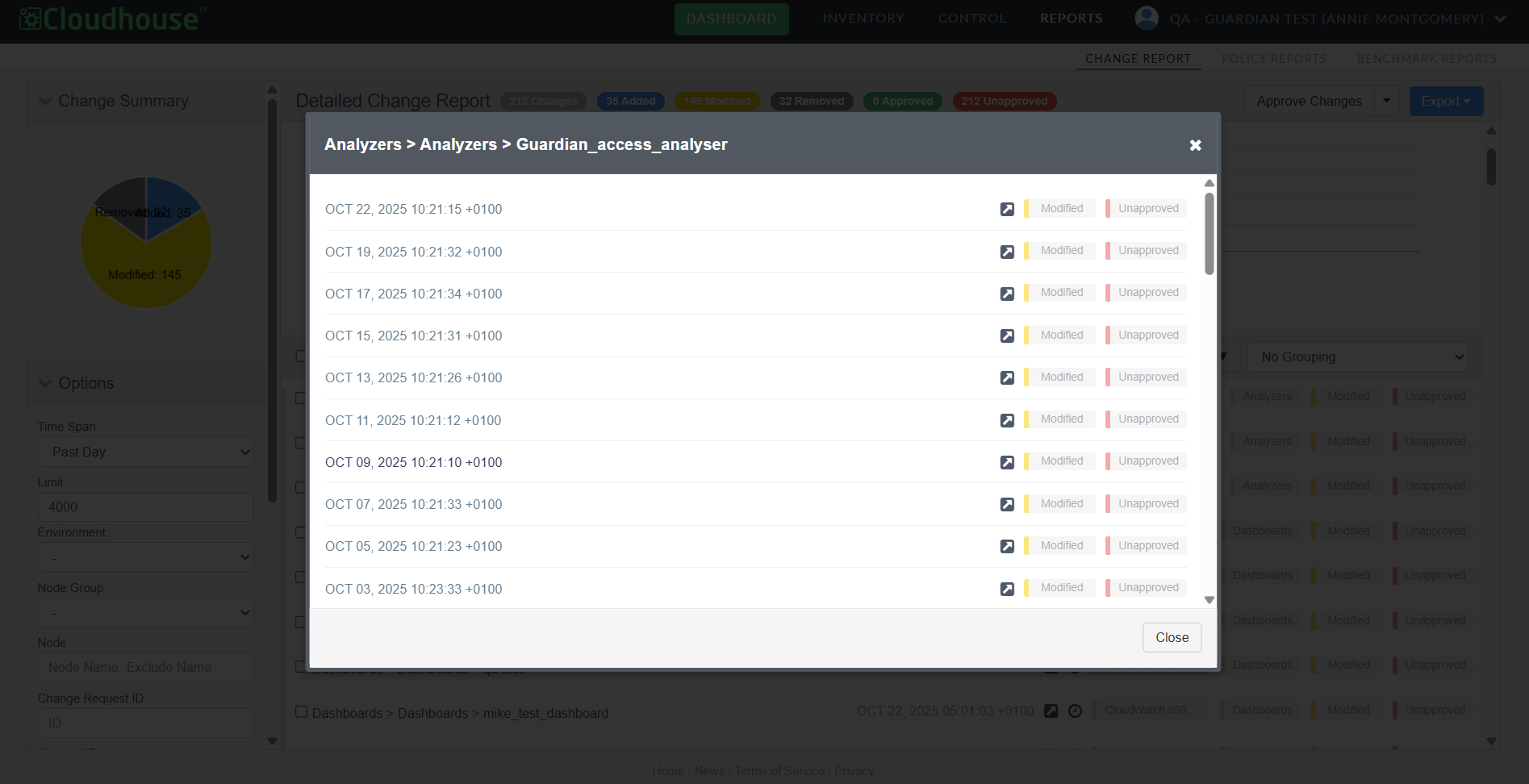
View Entire Change History
You can now view the entire history of a change directly within the Change Report tab using the new View History button (![]() ).
).
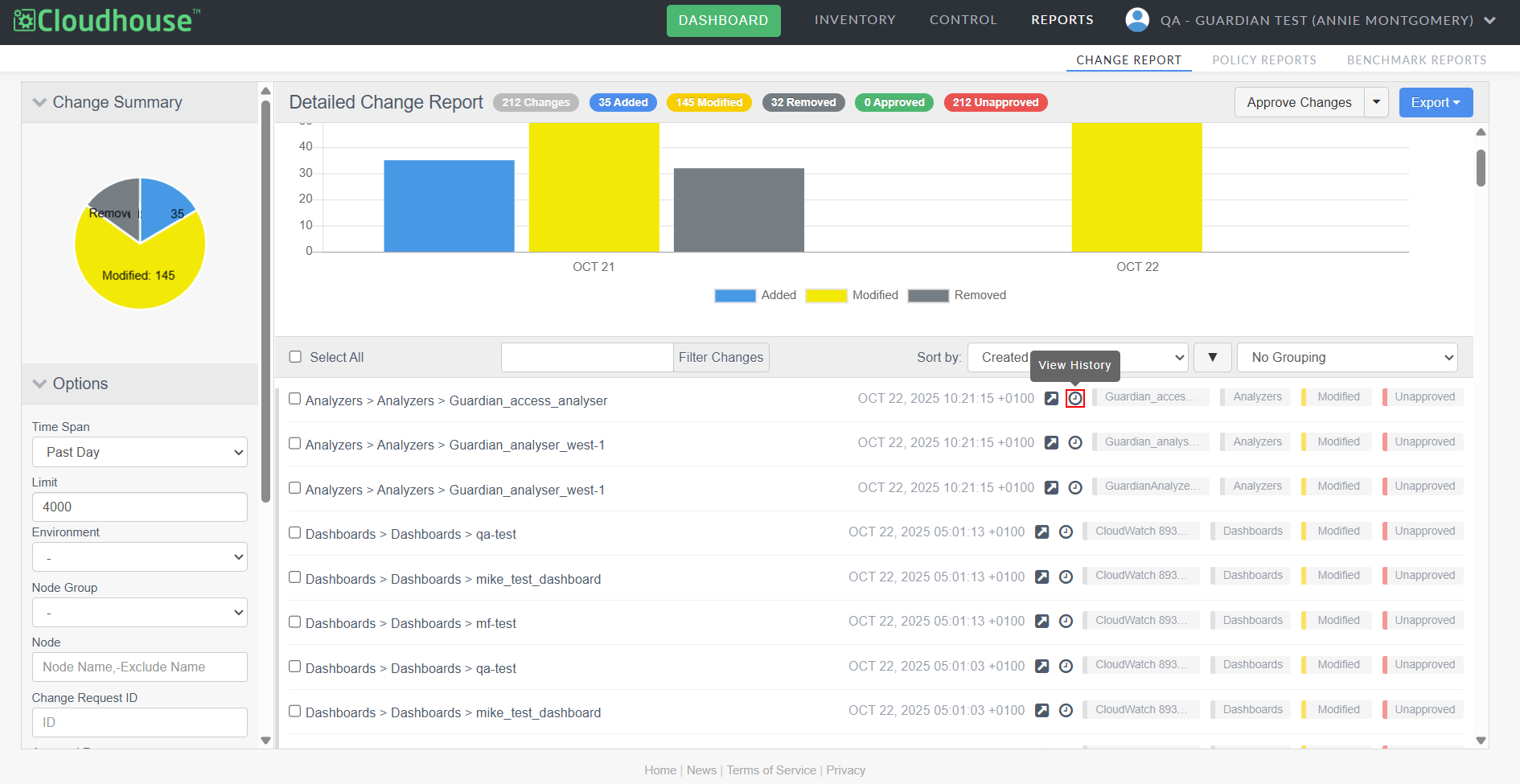
Previously, investigating a specific change required manually adjusting filters and timelines, disrupting workflow. This enhancement allows you to explore all changes made to a configuration item since its inception, without losing your place in the report.
Note: For .txt files, a file diff comparison is also available for modified items, making it easier to track precise changes.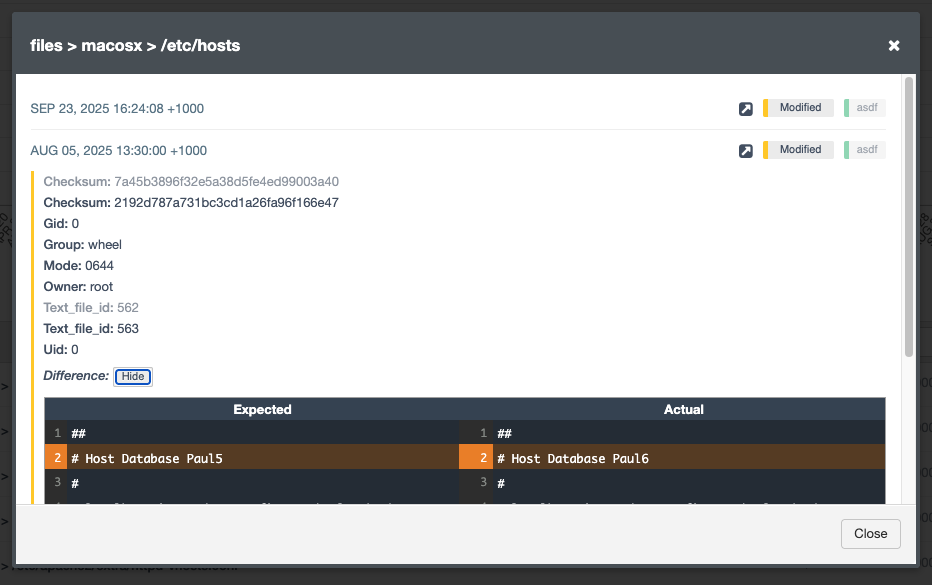
Role-Based Visibility for Change Reconciliation Functionality
To strengthen security and improve usability, the Manual Change Reconciliation functionality (introduced last release) has been updated to support role-based visibility. This enhancement ensures that only users with appropriate Administrative privileges can access sensitive approval actions within the Change Report tab.
Tip: For more information on Manual Change Reconciliation, see Manual Change Reconciliation.
For a full breakdown of the permissions, see the following list:
-
The Manual Change Reconciliation controls (e.g. approve/unapprove) are now hidden from users with the roles ‘Analyst’ and ‘Member’.
-
Analysts and Members can still view the Change Report tab, but cannot perform reconciliation actions.
-
Members must be explicitly granted permission to a node group to view associated changes (this behavior remains unchanged).
Tip: For more information on user roles in Guardian, see Users.
Fixed Issues
The following issues have been fixed within this release of the Guardian web application.
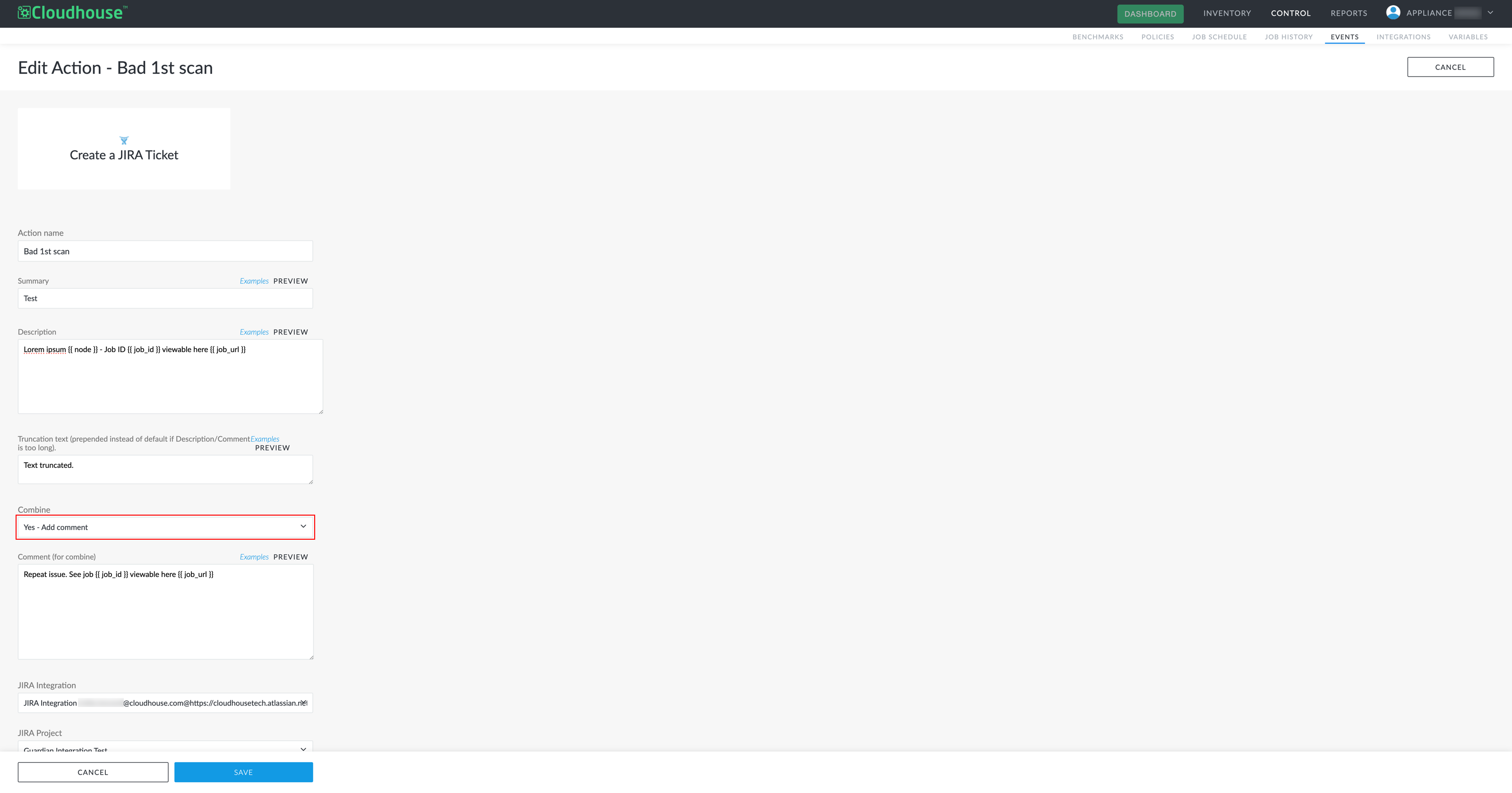
| NEW GWB-6381 – Combine Feature Fails Due to Deprecated Endpoint | |
|---|---|
| Affects Versions: V3 (onwards) | Fix Version: V3.60.1 |
| Problem: |
If you had a Jira integration set up and were to configure an action to occur when a specific event happened, setting the Combine drop-down to 'Yes - Add Comment' or ‘Yes - Add Label’ was resulting in a 410 error being returned when the action was triggered. Tip: For more information on event actions, see Actions. |
| Solution: |
The API endpoint previously used by the Combine feature was deprecated by Jira, causing the 410 error. We have now migrated the integration to use the new Jira endpoint, ensuring the Combine feature works as expected when an action is triggered. |
| GWB-6351 – Incorrect Priority Field Behavior in Scan Directories | |
|---|---|
| Affects Versions: V3.59.0 | Fix Version: V3.60.0 |
| Problem: |
When configuring scan options for a node group, editing the Priority field in the Scan Directories caused unexpected behavior. Tip: For more information on editing scan options, see Edit Scan Options. Complete the following steps to replicate the issue:
The Priority field in any newly generated scan directory row should be blank, allowing you to set it manually. |
| Solution: |
We have corrected the logic that populates the Priority field when new scan directory rows are auto-generated. The field now remains blank by default, ensuring consistent and predictable behavior during configuration. |
| GWB-4424 – Error Incorrectly Returned When Changing Guardian Email Address | |
|---|---|
| Affects Versions: V3 (onwards) | Fix Version: V3.60.0 |
| Problem: |
If you attempted to change the email address associated with your Guardian account, a 500 internal server error was being returned, even if the email address was formatted correctly and was not present in the system. |
| Solution: |
We have updated the error handling logic to ensure that when changing the email address associated with your Guardian account, if the email address is formatted correctly and is not present in the system already, a confirmation banner is displayed at the top of the page stating the change has been saved. Note: If the email address you are attempting to change to already exists within the system, or is not formatted correctly, an error message is displayed within a red banner as expected. |
| GWB-6252 – Inconsistent Application of Scan Options | |
|---|---|
| Affects Versions: V3.55.0 | Fix Version: V3.60.0 |
| Problem: |
Nodes were intermittently failing to appear as members of their correct node groups, resulting in inconsistent application of scan options. This caused the same node to be scanned using different configurations across runs, leading to unreliable and unpredictable scan results. Tip: For more information on scan options, see Scan Options. |
| Solution: |
Guardian now reliably computes node group membership and merges scan options correctly across all execution paths. This ensures that nodes are consistently scanned using the appropriate configuration, regardless of when or how the scan is triggered. |
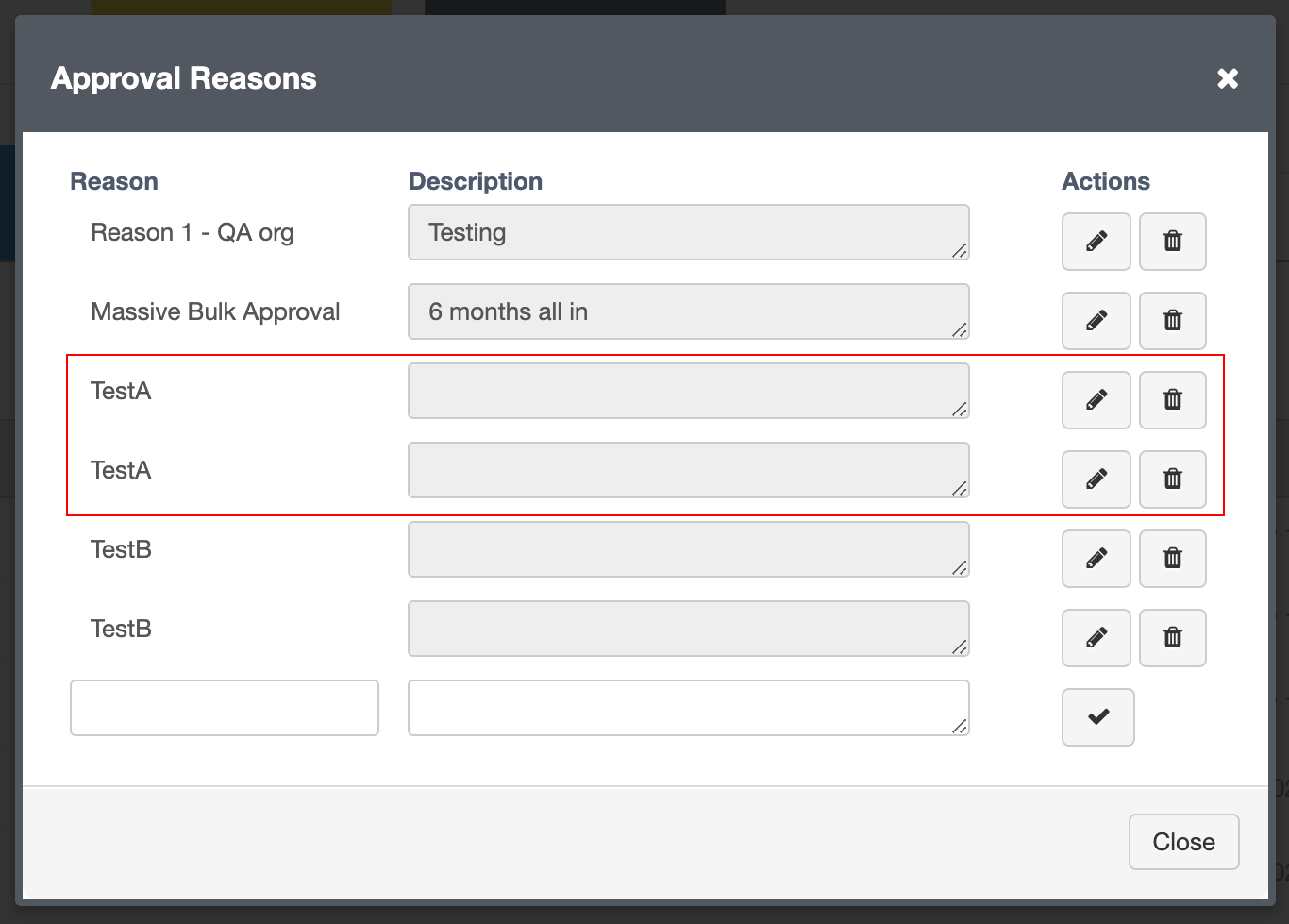
| GWB-6328 – Duplicate Change Reconciliation Reasons Allowed | |
|---|---|
| Affects Versions: V3.59.2 | Fix Version: V3.60.0 |
| Problem: |
When approving a change within the Change Reports tab, Guardian was incorrectly allowing you to add the same approval reason twice. This behavior is unintended, as each reason should be unique to maintain clarity and prevent confusion during reconciliation workflows. Note: This functionality is only visible to users with the 'Administrator' role. |
| Solution: |
Validation has been added to prevent the creation of duplicate approval reasons. If you attempt to add a reason that already exists, a confirmation prompt is now displayed, ensuring that all entries remain unique and meaningful. |
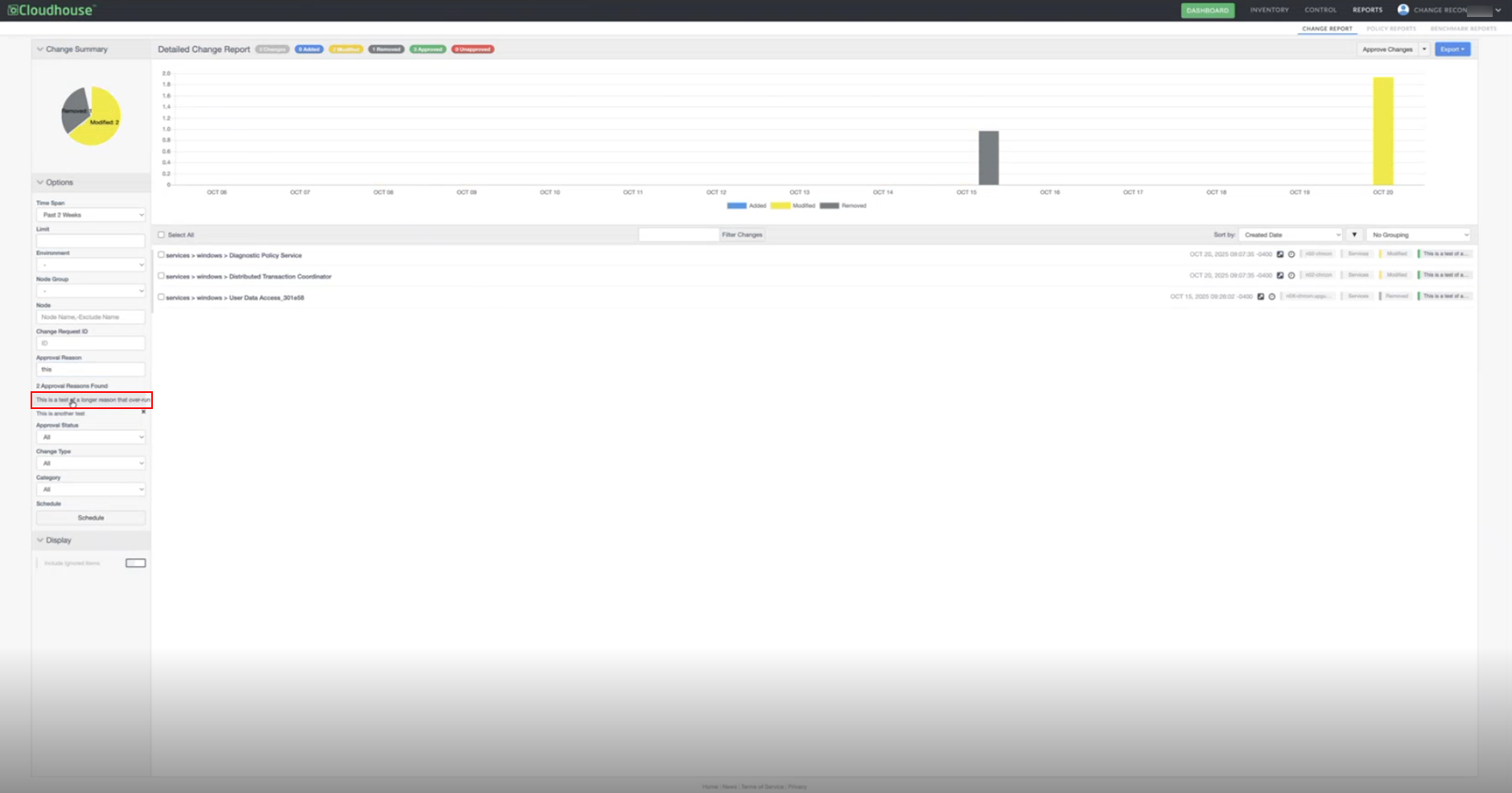
| GWB-6362 – Filter Clear Button Obscured by Sidebar Overlap | |
|---|---|
| Affects Versions: V3.59.0 | Fix Version: V3.60.0 |
| Problem: |
When filtering a change report via approval reasons, if the selected approval reason had a long title, you were unable to clear the filtered results. Complete the following steps to replicate the problem:
As a result, you would then be unable to clear the results as expected, as the button was not available to be selected. |
| Solution: |
The layout has been adjusted to ensure the Clear button [x] remains fully visible and clickable, regardless of the length of the selected filter name. This fix restores intuitive filter clearing behavior consistent with shorter filter names. |
| GWB-6317 – Missing Default Scan-Type in Multiple Scan Directory Entries | |
|---|---|
| Affects Versions: V3 (onwards) | Fix Version: V3.60.0 |
| Problem: |
When configuring the Scan Options for a node group, if you were to add multiple File type scan options consecutively, only the first scan directory entry would receive a default value for the Scan-Type drop-down list. Subsequent entries were left blank. If a file scan option is saved without a Scan-Type, it results in invalid configuration data. This causes the Linux Connection Manager to fail, ultimately leading to scan failures. Tip: For more information on scan options, see Scan Options. |
| Solution: |
The Scan Options have been updated to ensure that all new scan directory entries default to 'Config' for the Scan-Type drop-down list, not just the first. Additionally, validation has been added to prevent saving any scan option with a blank Scan-Type, ensuring consistent and valid scan configurations. Now, configuring the file scan options for a node group works as expected. |
| GWB-6310 – Incorrect LDAP Restart Notification | |
|---|---|
| Affects Versions: V3 (onwards) | Fix Version: V3.60.0 |
| Problem: |
Previously, if you updated your LDAP Settings (Account menu drop-down > Settings) a banner was displayed stating that an appliance restart was required, when no restart was necessary. Note: Only Guardian administrators can access the Settings page. For more information on this page, see Guardian Settings. |
| Solution: |
The misleading banner message has been removed. Saving LDAP settings no longer triggers a restart notification. Now, the following confirmation message is displayed in lieu, 'Settings successfully updated'. |
| GWB-5235 – Special Characters in Dynamic Node Group Queries | |
|---|---|
| Affects Versions: V3 (onwards) | Fix Version: V3.60.0 |
| Problem: |
Dynamic node group queries currently undergo a sanitization, which strips HTML tags and escapes special characters (e.g. ' Tip: For more information on dynamic node group queries, see Dynamic Group Queries. |
| Solution: |
Query matching logic has been updated to allow special characters to match against configuration item values. This ensures that queries like ' |
| GWB-6280 – Incorrect Variable Input Handling in ESXi Benchmark Rule 7.27 | |
|---|---|
| Affects Versions: V3.57.0, V3.58.0 | Fix Version: V3.60.0 |
| Problem: |
When attempting to modify variables for Rule 7.27 – (L1) Virtual machines must limit the size of diagnostic logs in the CIS VMware ESXi 8.0 Benchmark, the variable list and filter did not display any of the expected editable values, requiring users to manually input variable titles to proceed. Note: This behavior was traced to a benchmark misconfiguration in the CIS-provided XML, where variables were either duplicated or improperly defined, preventing Guardian from resolving them correctly. |
| Solution: |
Guardian has been updated to handle misconfigured benchmark variables more gracefully. Now, when modifying variables for a benchmark, the actual number of editable variables are displayed. Additionally, the variable list and filter box now show all available variables without requiring manual input of titles. You can now view and modify variables directly without guessing input formats. |
| GWB-6281 – Incorrect Variable Count Display in ESXi Benchmark | |
|---|---|
| Affects Versions: V3 (onwards) | Fix Version: V3.60.0 |
| Problem: |
When viewing an ESXi benchmark in Guardian, the button indicating the number of modifiable variables was incorrectly showing double the actual count. For example, if only two variables were present, the interface was displaying Modify 4 Values, leading to confusion. Tip: For more information on variables, see Benchmarks. |
| Solution: |
The logic in Guardian has been corrected to accurately reflect the number of unique modifiable variables. The system now accounts for variable ID uniqueness and avoids counting duplicates introduced by connection string handling. |
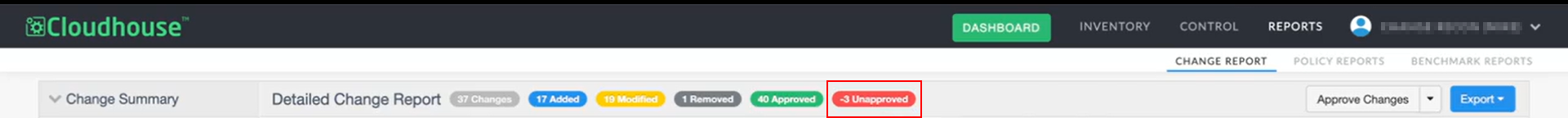
| GWB-6313 – Duplicate Approvals Incorrectly Change Approved / Unapproved Counts | |
|---|---|
| Affects Versions: V3.59.2 | Fix Version: V3.60.0 |
| Problem: |
Previously, in the Change Report tab, manually approving the same change twice - once with a change reason and once with a change request ID - would incorrectly increase the Approved count and decrease the Unapproved count. This resulted in misleading Approved and Unapproved totals. |
| Solution: |
The approval logic has been updated to ensure that each approval is only counted once in the Approved/Unapproved totals. Now, approving a change with both a change reason and a change request ID results in a single approval being counted, and the Approved/Unapproved totals remain accurate. |
Linux Agent V5.48.0
Here's what's included in V of the Linux Agent as part of the October 2025 quarterly release.
New Features
There are no new features included within this release of the Linux Agent.
Other Enhancements
There are no additional enhancements included within this release of the Linux Agent.
Fixed Issues
The following issues have been fixed in this release of the Linux Agent.
| NEW GLA-911 – RPM Package Parsing in Guardian Node Scan | |
|---|---|
| Affects Versions: V5 (onwards) | Fix Version: V5.48.0 |
| Problem: |
Guardian’s node scan logic assumed that RPM packages always include three components:
|
| Solution: |
We have updated the Agent logic to handle packages with any number of arguments. All installed RPM packages now appear in the scan regardless of format. This ensures accurate inventory and prevents gaps caused by non-standard RPM installations. |
GWB-908 – F5 Parser Enhancement for tcl Token |
|
|---|---|
| Affects Versions: V5.45.0 | Fix Version: V5.48.0 |
| Problem: |
A critical issue was identified where the F5 parser failed to handle configurations containing the |
| Solution: |
The F5 parser has been enhanced to support the |
Windows Agent V5.22
Here's what's included in V5.22 of the Windows Agent as part of the October 2025 quarterly release.
New Features
There are no new features included within this release of the Windows Agent.
Other Enhancements
There are no additional enhancements included within this release of the Windows Agent.
Fixed Issues
No issues have been fixed in this release of the Windows Agent.